BEWARE! YOUTUBE VIDEOS PROMOTING CRACKED SOFTWARE DISTRUBUTE LUMMA STEALER
📗 Date: 09 Jan, 2024
Source: The Hackers News
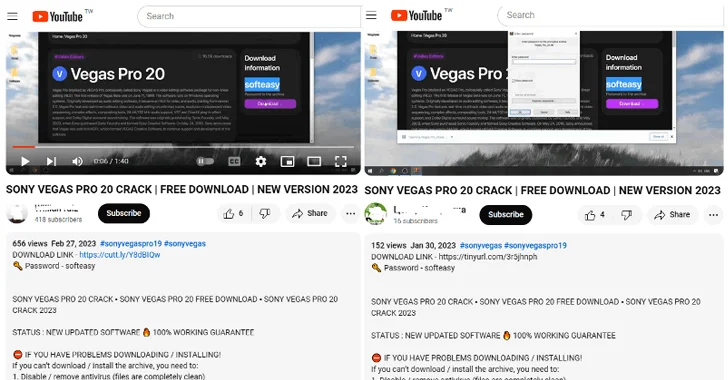
Threat actors are resorting to YouTube videos featuring content related to cracked software in order to entice users into downloading an information stealer malware called Lumma.
“These YouTube videos typically feature content related to cracked applications, presenting users with similar installation guides and incorporating malicious URLs often shortened using services like TinyURL and Cuttly,” Fortinet FortiGuard Labs researcher Cara Lin said in a Monday analysis.
This is not the first time pirated software videos on YouTube have emerged as an effective bait for stealer malware. Previously similar attack chains were observed delivering stealers, clippers, and crypto miner malware.
In doing so, threat actors can leverage the compromised machines for not only information and cryptocurrency theft, but also abuse the resources for illicit mining.
In the latest attack sequence documented by Fortinet, users searching for cracked versions of legitimate video editing tools like Vegas Pro on YouTube are prompted to click on a link located in the video’s description, leading to the download of a bogus installer hosted on MediaFire.

The ZIP installer, once unpacked, features a Windows shortcut (LNK) masquerading as a setup file that downloads a .NET loader from a GitHub repository, which, in turn, loads the stealer payload, but not before performing a series of anti-virtual machine and anti-debugging checks.
Lumma Stealer, written in C and offered for sale on underground forums since late 2022, is capable of harvesting and exfiltrating sensitive data to an actor-controlled server.
The development comes as Bitdefender warned of stream-jacking attacks on YouTube in which cybercriminals take over high-profile accounts via phishing attacks that deploy the RedLine Stealer malware to siphon their credentials and session cookies, and ultimately promote various crypto scams.
It also follows the discovery of an 11-month-old AsyncRAT campaign that employs phishing lures to download an obfuscated JavaScript file that’s then utilized to drop the remote access trojan.
“The victims and their companies are carefully selected to broaden the impact of the campaign,” AT&T Alien Labs researcher Fernando Martinez said. “Some of the identified targets manage key infrastructure in the U.S.”